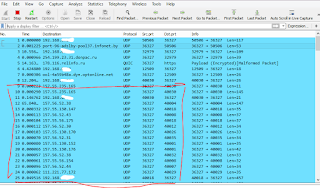
If we want to keep an eye on our Skype traffic to see the IPs of our Skype contacts, we can set up a very simple filer udp.srcprt==SKYPEPORT. Skype seems to exchange keepalive messages with all contacts currently showing as green (online) or yellow (away).
However, Skype also exchanges keepalive messages with the Microsoft servers and does alot of housekeeping stuff in the background, and the traffic to and from the Microsoft servers is very voluminous, and makes it hard to see traffic coming and going to and from our online contacts.
For example, in the image below, the conversation with a couple of MS servers is taking up half of the available screen area.
That is fine, but if you have Wireshark scan the traffic continuously, you can end up with hundreds of those server chit-chat messages obscuring the traffic to individual Skype users.
Cleaning up the traffic with a display filter
To screen out the traffic to any known MS servers, I simply turn on the Wireshark with my display filter being udp.srcprt==SKYPEPORT (in my case it is udp.srcport == 36327 ), and I record about 30 minutes worth of traffic. I then take note of the most commonly used IPs (which are probably server traffic).
- For example, I have 10 entries for 157.56.52.44, which belongs to Microsoft, etc.
- I also notice that I have entries for 157.56.52.44, 157.56.52.65, 157.56.52.89, 157.56.52.108, etc. So,the subnet 157.56.52.0/24 can be assumed to be taken by MS servers.
Next, I notice that I have 157.55.56.151, 157.55.58.154, 157.55.36.15, etc also being server traffic. So, I conclude that subnet 157.56.0.0/16 also seems to be dedicated to MS servers.
So, it is now possible for me to filter out all traffic going to the subnet 157.56.0.0/16. So, my filter will be ((udp.srcport == 36327 ) &&!(ip.addr == 157.55.0.0/16) . If I keep analyzing the remaining displayed traffic, I will find additional patterns of traffic that indicate various IPs assigned to MS servers. As soon as I find an IP belonging to a MS server, I put a filter on that entire /24 subnet.
For my traffic, I ended up filtering out the following subnets:
- 111.221.77.0/24
- 157.55.0.0/16
- 157.56.0.0/16
- 65.55.0.0/16
- 64.4.0.0/16
Here is the full display filter for these subnets:
(((((udp.srcport == 36327 ) && !(ip.addr == 111.221.77.0/24)) && !(ip.addr == 157.55.0.0/16)) && !(ip.addr == 64.4.0.0/16)) && !(ip.addr == 157.56.0.0/16)) && !(ip.addr == 65.55.0.0/16)
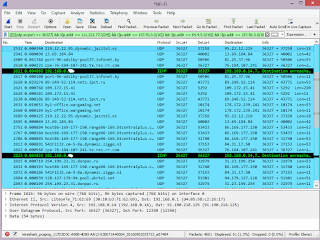
Here is the resulting capture:
For this capture, a total number of packets captured was 4601, and number of displayed packets is 61, so now we can easily see on just one or two screens ONLY those packets that are of real interest (they show IPs of Skype users in our contact list). Now it is much easier for us see the data we are targeting.
10 minutes interval for keepalive packets
If I am need to find out an IP of a particular Skype user, this user will
1) need to be in my contact list
2) need to be on status Available or Away (I think! I am not sure if the logged off users show up)
If those two conditions are met, I can turn on Wireshark, install my "interesting traffic" filter, and just watch the packets roll in. Based on my observation, the keepalives are set to ALL Skype contacts that are Available or Away with the interval of about 10 minutes.
So, if you do nothing but sit and quietly capture packets for 30-40 min, you should be able to get a list of IPs of all reach-able users in your contact list.
You can then filter by conversation if you want traffic to a particular IP grouped together for you.
Setting up capture filter
If you really do run Wireshark for 40 minutes, you may end up with a very heavy capture file with tens of thousands of packets and a file size of 80MB or more. This is not needed if you are not interested in examining any other traffic from that capture.
So, I recommend installing a capture filter, so Wireshark only captures Skype traffic and nothing else. This should reduce your capture file size dramatically.
So, whatever your Skype port is, just create a new capture filter port SKYPEPORT (in my case, port 36327), and apply that capture filter to the interface from which you are capturing
I ran Wireshark with this capture filter for 2 hours this morning, and my total number of packets captured is 1916. Total file size is 277Kb. I was able to capture about 78 IPs, which makes me think that even IPs of users not online were captured, because only about 15 of my friends were Available or Away at that time.
So, the bottom line is that if the user of your interest is in your Skype contacts, you can capture his/her IP even without entering into voice or video conversation.